The Cloud Management Gateway is an integral part of the cloud computing ecosystem that enables companies to achieve seamless device management and security in the cloud. Companies can now securely manage devices connected to the internet via the Cloud Management Gateway, ensuring that they are always up-to-date and safeguarded from threats.
Image 1:
This first image shows how the Cloud Management Gateway is being used in Azure, where it is used to manage device connections in the cloud. The Azure portal has built-in support for the Cloud Management Gateway and it is easy to configure and use.
Image 2:
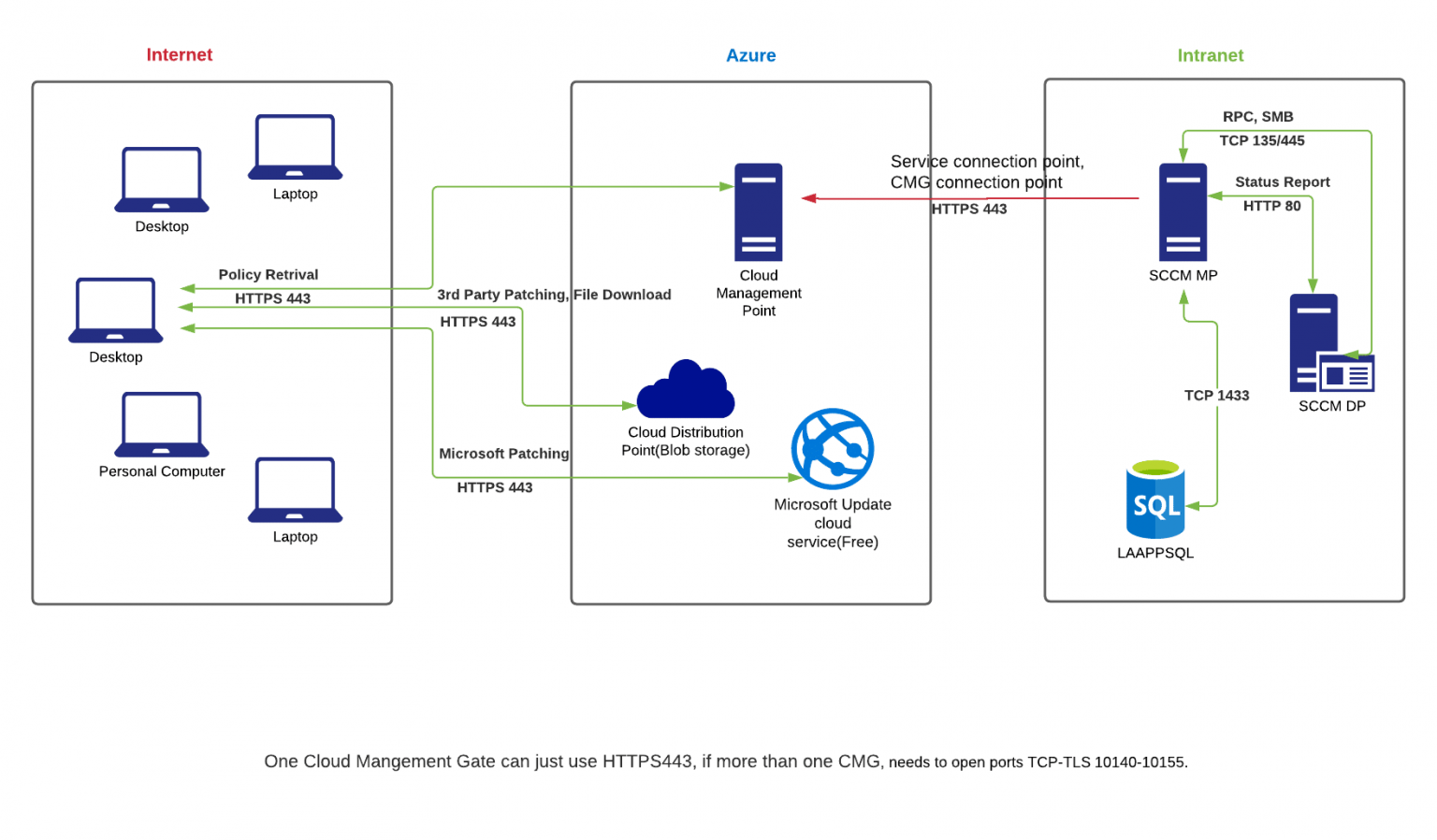
The second image shows a diagram of how the Cloud Management Gateway architecture works with the SCCM DMZ IBCM. The Cloud Management Gateway is used to provide a secure and reliable connection between the on-premises environment and the cloud.
Image 3:
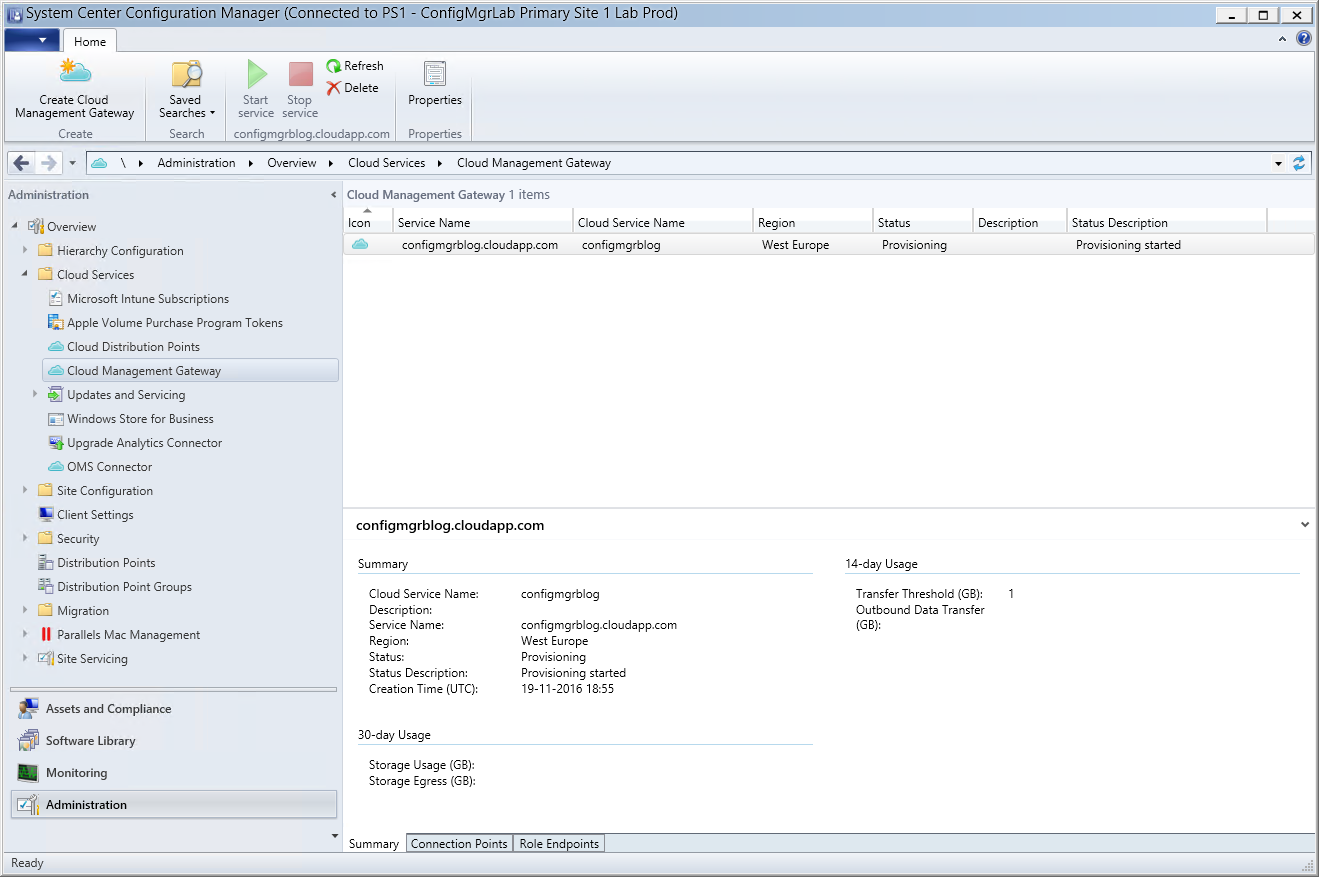
The third image shows the configuration options available in the ConfigMgr Cloud Management Gateway. Administrators can configure the gateway to require authentication, limit access to specific applications, and enable or disable specific protocols.
Image 4:

The fourth image highlights how the Cloud Management Gateway can be secured to ensure that device connections to the cloud are protected from malicious actors. The Cloud Management Gateway provides a secure entry point to the cloud that is monitored and protected by security policies, ensuring that only authorized users and devices are allowed to connect.
In conclusion, the Cloud Management Gateway is an essential component of any cloud computing strategy that aims to manage and secure devices connected to the internet. By leveraging the power of the cloud, companies can scale their device management and security efforts to achieve business objectives efficiently.